Introduction
In the digital age, cloud computing has revolutionized the way businesses operate. Its scalability, flexibility, and accessibility have made it an indispensable tool for organizations of all sizes. However, with the convenience of cloud computing comes the challenge of ensuring robust security measures are in place. As businesses increasingly migrate their operations to the cloud, the need to address and overcome cloud security challenges becomes paramount. In this article, we’ll explore some of the key challenges faced in cloud security implementation and strategies to overcome them.
Definition
The methods and procedures used to safeguard infrastructure, data, and apps that are housed and used in cloud environments are together referred to as cloud security. It includes protections against data breaches, illegal access, and other dangers, guaranteeing the privacy, availability, and integrity of cloud resources. Identity and access control, encryption, frequent audits, and adherence to best practices are all necessary for effective cloud security.
Understanding the Challenges
Implementing effective security measures in the cloud involves addressing various challenges, including:
Data Breaches:
- Unauthorized access to sensitive data poses a significant threat in the cloud environment.
- Data breaches can occur due to weak authentication, insufficient encryption, or misconfigured access controls.
Compliance and Regulatory Requirements:
- Different industries are subject to specific regulatory standards and compliance mandates.
- Ensuring compliance with regulations such as GDPR, HIPAA, or PCI DSS adds complexity.
Insider Threats:
- Employees or authorized users with malicious intent can pose a substantial risk.
- Insider threats can take the form of data theft, sabotage, or inadvertent disclosure of private information.
Shared Responsibility Model:
- Cloud service providers (CSPs) follow a shared responsibility model, where they manage certain aspects of security, while customers are responsible for others.
- Understanding and delineating responsibilities between the CSP and the customer is crucial for effective security implementation.
Security Misconfigurations:
- Misconfigurations in cloud services and infrastructure can create vulnerabilities that attackers exploit.
- Common misconfigurations include improper access controls, unsecured storage buckets, and overly permissive network settings.
Strategies for Overcoming Cloud Security Challenges:
Comprehensive Risk Assessment:
- Conduct a thorough risk assessment to identify potential security threats and vulnerabilities.
- Assess the sensitivity of data stored in the cloud and evaluate the impact of potential security breaches.
Encryption and Access Controls:
- Implement robust encryption mechanisms to protect data both at rest and in transit.
- Utilize strong access controls, including multi-factor authentication (MFA) and role-based access control (RBAC), to restrict unauthorized access.
Continuous Monitoring and Auditing:
- Employ automated monitoring tools to continuously monitor cloud environments for suspicious activities.
- Conduct regular audits to ensure compliance with security policies and regulatory requirements.
Employee Training and Awareness:
- Provide comprehensive training to employees on best practices.
- Encourage a security-conscious culture to reduce the possibility of insider attacks and human mistake.
Cloud Security Solutions:
- Invest in robust cloud security solutions that offer features such as threat detection, intrusion prevention, and data loss prevention.
- Leverage cloud-native security services provided by CSPs, such as AWS GuardDuty or Azure Security Center.
Collaboration with CSPs:
- Establish a partnership with your CSP to understand their security offerings and capabilities.
- Work closely with the CSP to ensure alignment of security measures and responsibilities outlined in the shared responsibility model.
Regular Security Updates and Patch Management:
- Stay updated with the latest security patches and updates released by both the CSP and third-party vendors.
- Implement a robust patch management process to promptly address security vulnerabilities and mitigate risks.
Growth Rate of Cloud Security Market
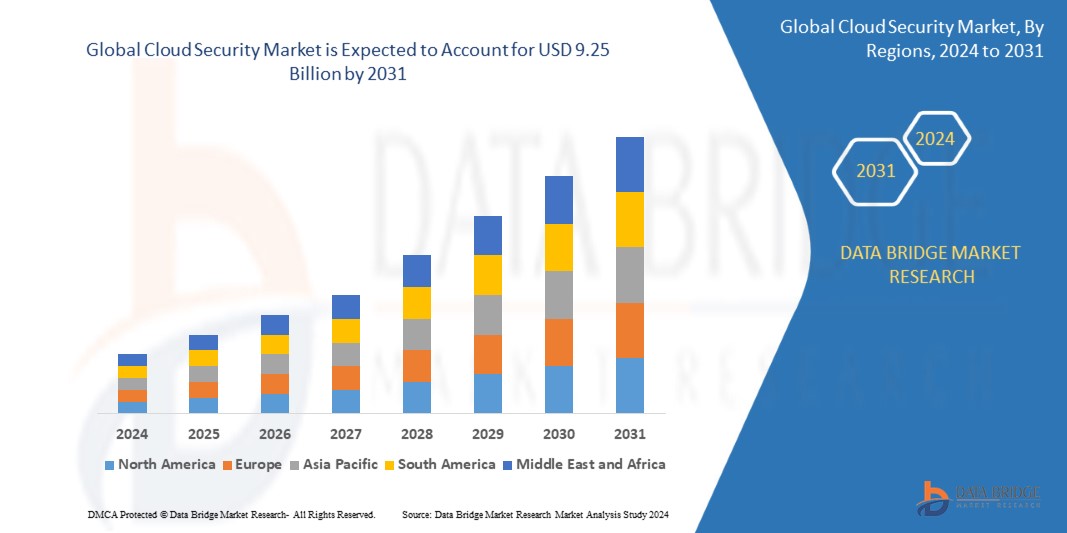
According to Data Bridge Market Research’s analysis, the global cloud security market is predicted to grow at a compound annual growth rate (CAGR) of 17.2% between 2024 and 2031, from its estimated valuation of USD 2.2 billion in 2023 to USD 9.25 billion by 2031.
Conclusion
While the benefits of cloud computing are undeniable, ensuring the security of cloud environments remains a critical concern for businesses. By understanding the challenges associated with cloud security implementation and adopting proactive strategies, organizations can effectively mitigate risks and safeguard their data and resources in the cloud. From comprehensive risk assessments to leveraging advanced security solutions, addressing cloud security challenges requires a multifaceted approach. By prioritizing security and staying vigilant, businesses can confidently harness the power of the cloud while minimizing security risks.
To read more click here.
https://www.databridgemarketresearch.com/reports/global-cloud-security-market